Overview
Details on how to source and purchase software and cloud computing services at UCSF.
The BearBuy Process of Software and Cloud Computing Purchases
The Software & Cloud Computing Form in BearBuy is required to purchase:
- Cloud computing services, defined as a model for delivering applications, information, infrastructure or services as pools of resources via the internet (for definitions and examples, refer to IT Security Cloud Computing Guidance)
- New software or software licenses (other than the exclusions listed below)
- Software license agreement renewal or software maintenance contract renewal when the supplier has access to UC PHI or UC non-public information, information resources or protected information (defined in UC Procurement Services Appendix DS), or the scope of work has changed.
Exclusions
The following types of software do NOT need to be ordered on the BearBuy Software form:
- Single-user desktop software that does not interface with other UCSF systems or connect to the internet to store or transmit UCSF data.
- Software embedded in hardware or equipment.
- Software provided by UCSF IT, e.g., Microsoft Office 365 or GlobalProtect VPN -- for assistance, contact IT Service Desk at (415) 514-4100.
- SAS, SAS Server, JMP, SPSS licenses (all provided by IT) please contact Sudeep Basnet [email protected].
- GitHub, also provided by IT, contact Jessica Hilt, [email protected] – there are 2 types of GitHub licenses, more info here: GitHub Enterprise Cloud and GitHub Enterprise Server (On-Premises).
- Adobe Creative Cloud and Acrobat Pro enterprise term license accounts are provided by IT. Please visit UCSF Adobe Licensing. For assistance, contact Jerry Tung [email protected].
- For Adobe Software outside of Creative Cloud and Acrobat, please contact [email protected] for a quote, but if you want a license for components of Creative Cloud (e.g., Photoshop, Illustrator), just buy Creative Cloud through ETLA (Jerry Tung) and use the components you need – this is more cost-effective than buying individual licenses through Adobe VIP.
- UCSF Library has links to software (including MATLAB, ArcGIS, Stata) available with academic pricing through other sources.
| SOFTWARE | CONTRACTED VENDOR | PURCHASING METHOD | CONTACT FOR QUOTES |
|---|---|---|---|
| Microsoft, Netskope, Microfocus | Dell | Dell punch-out | [email protected] |
| Software available from SHI (all other software under $100K) | SHI | SHI punch-out | [email protected] |
| GraphPad Prism (two-license minimum) | CDW-G | CDW-G punch-out | [email protected] |
| Canva | NA | UCSF IT Service Ticket | Please visit UCSF IT's Purchasing Canva License** |
| EndNote* | Clarivate | Non-Catalog Form/ Amount-based PO | Lauren Zellner (480) 550-8573 or Boaz Levin (215) 837-7637 |
| Twilio | Twilio | Non-Catalog Form/ Amount-based PO | Laura Lundahl Baga |
| QGenda | QGenda | Non-Catalog Form/Amount-based PO | Patrick Duffy |
*Pricing for EndNote from Clarivate is currently $106 for staff/faculty/student licenses, $90 for upgrades of existing licenses; no additional discounts for bulk buys.
** Canva license requests and purchases are managed by UCSF IT.
Do not use the BearBuy Payment Request Form or UCSF Procurement Card (P-card) to purchase software, software licenses or cloud computing services. The "subscriptions" option on the Payment Request Form is intended only for periodicals, such as newspapers or magazines.
UCSF IT Security Risk Assessment
According to the UC Electronic Information Security policy (BFB IS-3), all systems that create, store, process, or transmit data internally at UCSF or externally through a supplier or other third party must be assessed for risk. This applies to all UCSF data, including but not limited to PHI, PII, PCI, RHI, FERPA and other restricted or sensitive data. UCSF prioritizes the highest-risk systems for a full security risk assessment.
If you are purchasing a software product or cloud service that creates, stores, processes, or transmits UCSF data, a full security risk assessment may be required.
- Before placing your order in BearBuy, contact IT Security at [email protected] to determine whether a risk assessment is required.
- For more information on the risk assessment process, including how to request an assessment, what supporting documents are required, and what to expect during the process, visit the IT Security Risk Assessment page.
BearBuy Instructions - Software & Cloud Computing Form
When you are ready to place your order, follow the instructions below.
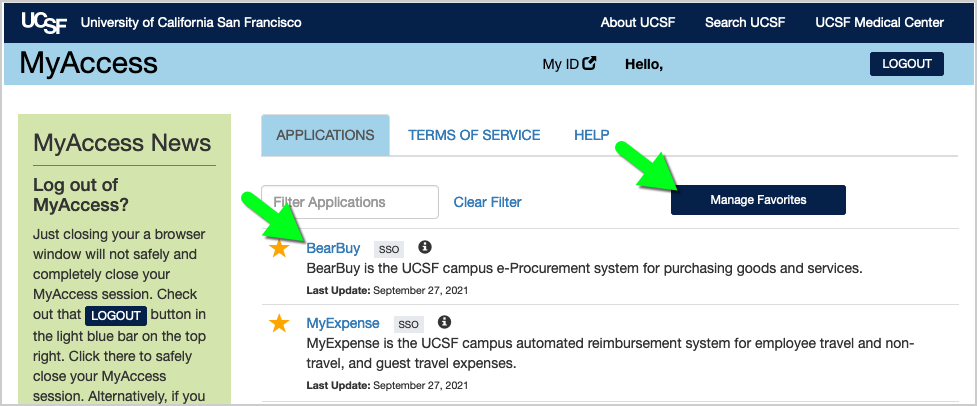
Accessing BearBuy
- Login to your UCSF MyAccess account.
- Click on the BearBuy link to open the application.
- Note: You may need to click the Manage Favorites button in UCSF MyAccess to view the complete list of applications.
Navigating to the Software & Cloud Computing Form
- In BearBuy, scroll to the bottom of the homepage to find the Software & Cloud Computing Form (in the Forms for Specific Purchases section).
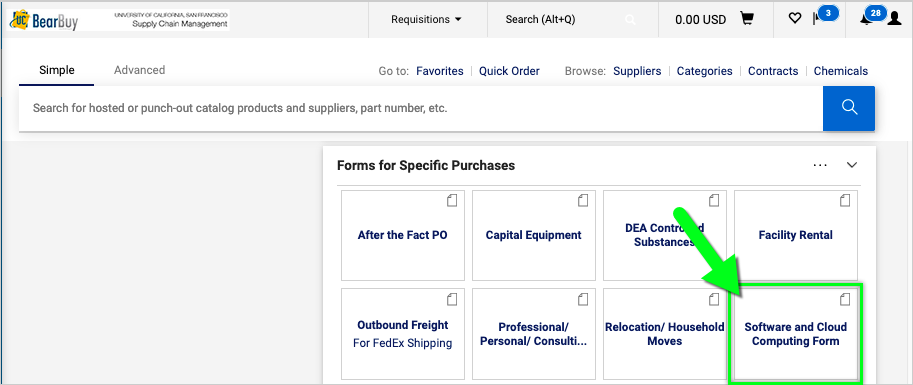
- Click on the form to open it.

- The form opens in your browser window.
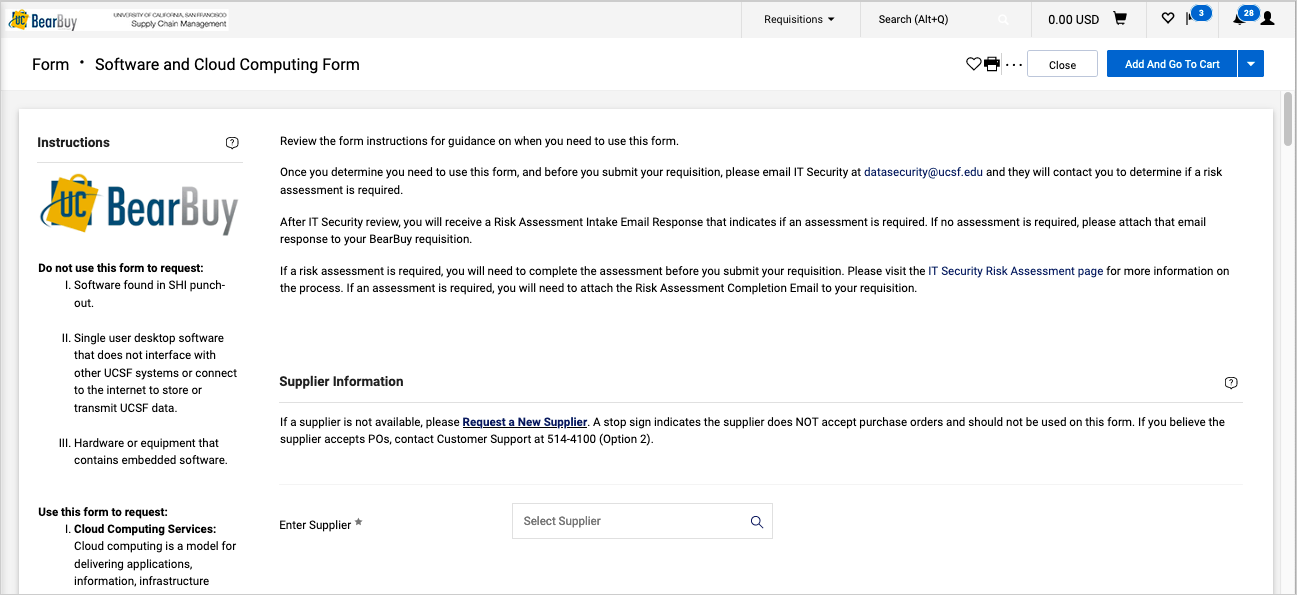
Completing the Software & Cloud Computing Form
Read the instructions on the left side of the form and enter all required information indicated with an asterisk (*) on the form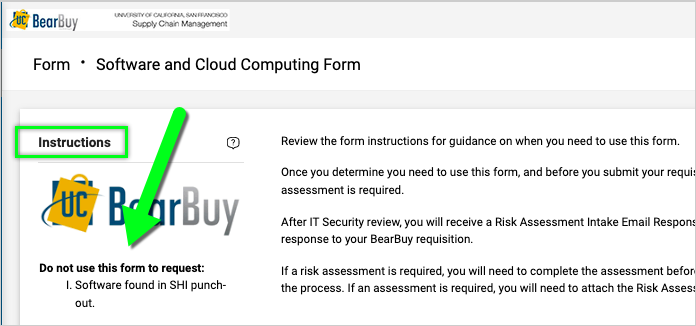
- IT Security Risk Assessment: Contact IT Security at [email protected] to determine if a Risk Assessment is required. Complete and attach the Risk Assessment Completion Email (provided to you by IT Security) to your form in BearBuy before submitting the order. Otherwise, attach the Risk Assessment Intake Email Response from IT Security indicating that no assessment is required.
- Supplier: Start typing the supplier name and select it from the list that appears. Otherwise, submit the appropriate Supplier Registration form to [email protected] to request to add the new supplier to BearBuy.
- Fulfillment Address: This is the supplier's address where the order will be fulfilled. You may be able to select a different address if the Pencil icon appears. To add or update an address, email [email protected] for assistance.
- Supplier Contact: Enter the name, phone number and email address of your supplier contact.
- Department Information: Specify the Department Name and the department technical contact who will answer technical questions about the software purchase.
- Software Information & Justification: Enter the start and end date for your software and a brief description of the software or service, including but not limited to (1) what it will be used for and (2) whether and what kind of UC data will be hosted, stored or accessed by the supplier. When using an established UC agreement, enter the contract information (title, reference, number, etc.).
- Statement of Work: When purchasing services, establish a Statement of Work. Determine the payment structure based on completion of work, achievement of project milestones, or phases of work or provision of acceptable deliverables.
- HIPAA: Select "Yes" only if the supplier will have access to Protected Health Information (PHI). Otherwise, select "No."
- Note: If UC PHI will be transmitted or stored outside the University's system, please initiate the IT Security Risk Assessment as early as possible so as to not delay the release of your PO.
- FWFW: Select "FWFW" only if the supplier will provide services at a location owned or leased by UC. Otherwise, select "No."
- License or Service Agreement: Indicate whether this transaction results from a current or prior License or Service Agreement with the supplier and if yes, provide the PO or Agreement number, if known.
- Estimated Cost: Enter the total estimated dollar value of the software or service in the "Not-to-Exceed Price" field.
- Commodity Code: Select a Commodity Code from the dropdown list, such as 00256-Software<$5,000/Cpy-52305. During checkout, you can override this value, see Accounting Guidance below.
- Conflict of Interest: Select the radio button to agree to the statement; otherwise, contact your Department-Assigned Buyer prior to submitting the form if you believe the purchase may involve a conflict of interest.
- Price Reasonableness & Source Selection: Only complete this section for federally funded purchases ≥ $50,000 (including tax and shipping) and/or non‐federally funded purchases ≥ $100,000 (excluding tax, but including shipping). For orders > $100,000, please contact your SCM Department-Assigned Buyer prior to submitting the form. If selecting Non-Formal Quotes, attach three (3) qualifying competitive quotes to the Attachments section at the bottom of the form. For details, read the Price Reasonableness and Source Selection FAQs.
- Attachments: Attach any required or applicable documents, such as the IT Security Risk Assessment or Statement of Work. Note: External Attachments will be sent to the supplier along with the purchase order (PO) and remain viewable within BearBuy.
- When finished, select the Add And Go To Cart button located at the top of the form (or select "Add to new Cart" from the dropdown). Note: To add multiple forms to your cart, select "Add To Cart and Return" from the dropdown.
Submitting your order
- After adding the form(s) to your shopping cart, check/uncheck the Taxable box to indicate whether the line item is taxable. The taxability of software can vary. Software delivered through physical media (e.g., CD, thumb drive) is Taxable; software delivered electronically is NOT taxable.
- When purchasing software for campus (business unit "SFCMP"), review the Accounting Guidance below to determine the appropriate Account. If necessary, click the Proceed to Checkout button at the top of your screen and enter the Account in the Accounting Codes section on your order.
- Next, assign the cart to your department’s Requester to complete the checkout process and submit the requisition.
- After the requisition is submitted, the order will route to your department’s Requisition Approver for approval (typically, for orders > $500).
- Finally, the requisition will route to your SCM Department-Assigned Buyer to review/approve.
- Once the requisition is fully approved, a purchase order (PO) and any External Attachments will be sent to the supplier.
Accounting Guidance
When purchasing software for campus (business unit "SFCMP"), review the matrix below to assign your BearBuy order to the appropriate Account. After adding the Software form to your cart, click Proceed to Checkout to enter the Account in the Accounting Codes section of your order. This will override the Commodity Code selected on the form.
- Note: Any software purchased by Agency Funds (2XXX series) can only be expensed; not eligible for capitalization.
- The four-digit equipment custody code is not needed in BearBuy for this type of purchase.
| SOFTWARE/SERVICE DESCRIPTION | ACCOUNT |
|---|---|
| Software Maintenance/Assurance Plan/Service Agreement (e.g., maintenance, help desk support, license fees, training, upgrading and enhancements) | 55053 |
| Hardware Maintenance/Assurance Plan/Service Agreement (e.g., maintenance, help desk support, license fees, training, upgrading and enhancements) | 55052 |
| Perpetual license, cost per license is $5,000 or more | 51323* (sponsored) or 52602* (non-sponsored) |
| Software System, value greater than $5,000 | 51323* (sponsored) or 52602* (non-sponsored) |
| Software/System, unit value less than $5,000 per copy | 52305 |
| Software purchased separately for an existing piece of inventorial equipment | 52311* |
| Consulting Services directly attributed to a specific software application; design of selected software (configuration, interfaces), coding, testing (parallel processing phase) | 51323* (sponsored) or 52602* (non-sponsored) |
| Consulting Services not associated with a specific software application | 55102 |
*capitalized expense
Contractual Risks Associated with Software Purchases
Part of what has been recognized in regards to cloud computing and software purchases is a particular exposure to contractual risk with such purchases. For example, it is quite common for such purchases to be accompanied by very easy-to-execute “click through” agreements, using Supplier terms and conditions.
“Click-through,” “shrink-wrap” and similar supplier terms/agreements may constitute legally binding agreements, binding UC to their terms. Acceptance of such terms as written could expose the University to unacceptable and costly risks, including but not limited to being liable for using infringing software; being liable for third party acts or omissions (i.e., a direct violation of a UC Standing Order); HIPAA violations; possible mishandling of sensitive data; intellectual property concerns; and non-compliance with laws/regulations/policies of Federal, State, UC, funding agency entities.
Such "click-through" agreements for software or services available on the Internet are not approved by UCOP or UCSF legal and procurement departments; moreover, only authorized individuals can enter into agreements for UC. Therefore, please avoid clicking-through on such agreements and instead please use the BearBuy Software & Cloud Computing Form to engage SCM in finalizing your transaction, including agreement terms that are compliant with regulations, UC policies, etc.
Consider using an established UC agreement that could help determine your supplier selection, improve product pricing, and offer better terms and conditions of sale. When using such an agreement, please enter the contract information (title, reference, number, etc.) in the box under “Software Information and Justification” on the BearBuy Software form.
Software Suppliers That Do Not Accept Purchase Orders
Software and cloud computing purchases can potentially expose the University to risk from legally binding agreements and data security. To mitigate this risk, BearBuy purchase orders (POs) should be created for software purchases. POs contain UC terms and conditions that are shared with suppliers, which can help protect University interests.
However, not all suppliers accept POs. These purchases require additional review by SCM and IT Security to determine if the software meets UC terms and conditions of purchase and IT Security standards before the purchase can be made.
If you have a software supplier that will not accept a BearBuy PO, follow the steps below to facilitate this review before the purchase:
- Complete the Software Purchase Form for Suppliers That Do Not Accept Purchase Orders
- Contact IT Security at [email protected] to confirm if an IT Security Risk Assessment is required for the purchase (but see exclusions listed above). Then, complete the IT Security Risk Assessment or obtain the Risk Assessment Intake Email Response (stating no risk assessment is required).
- Email the above form, IT Security documentation, and all other supporting documentation to SCM at [email protected].
- SCM will review all this information and coordinate with you on the purchase.
